If you’re a Virgin Media customer and you use a Super Hub or Super Hub 2 router to access the Internet, you should know that hackers can access your network and do whatever they want with your Web connection.
British security researcher Paul Moore is the one who identified the issue. He has reported it to Virgin and Virgin has reported it to the manufacturer, Netgear. However, since it could take months until the vulnerability is fixed, Moore has decided to publish an advisory to teach users how to protect themselves.
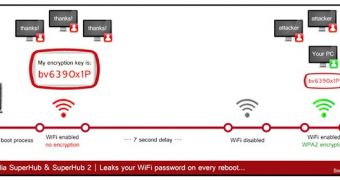
The expert has found that, when the Super Hub device is started, it takes around 1 minute to fully boot. In this timeframe, there’s a 7-second window in which the Wi-Fi is enabled without any kind of encryption.
During this 7-second window, an attacker could compromise the device. If you’re thinking that it’s impossible for someone to compromise the device in 7 seconds, you are wrong.
There are two other factors that enable an attacker to exploit these 7 seconds. One of them is the fact that devices are accessible by default via two IPs: 192.168.100.1 and 192.168.0.1. The second is the fact that all Super Hub and Super Hub 2 routers have a default password, “changeme,” which users rarely change.
With this information in hand, a hacker who’s in close range of the targeted network can access the device’s user interface and obtain the Wi-Fi encryption key from the “Security Settings” menu. The encryption key is in plain text, so it can be easily copied.
After the 7 seconds, encryption is enabled. However, if the attacker has already gained access to the encryption key, it doesn’t matter.
You’d think that such an attack is mitigated by the fact that an attacker doesn’t know when you’re about to start your router, and it would be inefficient for someone to just wait around for the right moment. However, Moore has demonstrated that a force reset could be triggered with a few lines of code.
Furthermore, the hacker doesn’t even need to manually perform the attack. Instead, he could use a Wi-Fi virus.
“Purely as a proof of concept, I created a self propagating version of this exploit. It searches for vulnerable access points/routers, forces a reboot, grabs the encryption key, connects to the hijacked network, forces any connected client machines to download the exploit and so the loop continues,” the researcher explained on his blog.
Once they gain access to the network, hackers can do whatever they wish: change DNS settings to redirect the user to arbitrary sites, intercept traffic, install malware, access files on the hard drive, and even hijack the printer and the webcam.
Until Virgin pushes out a firmware update for Super Hub and Super Hub routers to address the problem, there’s something users can do to mitigate a potential attack: change the default password.
For additional technical details on this Virgin Super Hub vulnerability and for a step-by-step guide on how to change the default password, check out Moore’s Rambling Rant blog.
 14 DAY TRIAL //
14 DAY TRIAL //