Canadian users have been hit hard by banking trojans during recent months, with US security vendor Proofpoint reporting about six different malware variants targeting users in this country, namely Dridex, Gootkit, Kronos, Ursnif, Vawtrak, and Zeus.
Banking trojans don't actually operate based on the user's country, but based on the financial institution they plan to spoof and steal money from. Of course, there will be some overlap between different banking trojans since most will target developed countries, where users have larger sums in their bank accounts.
What is strange is the fact that, in a short period of time, a large number of these banking trojans targeted users of Canadian financial institutions.
Spam links, macro malware, and OLE objects used to deliver payloads
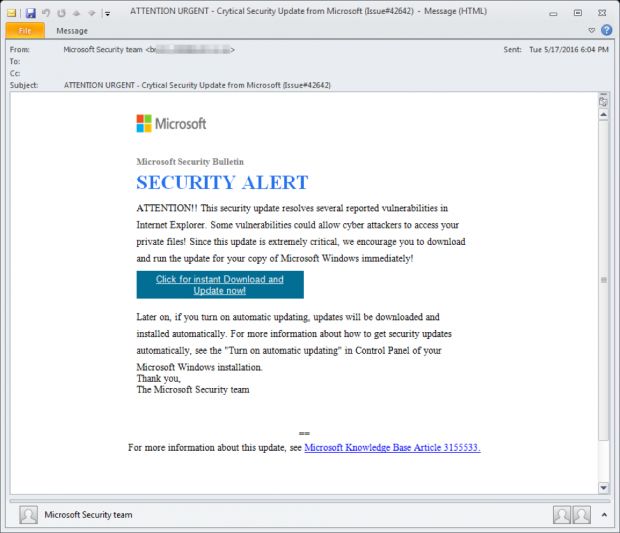
The first campaign Proofpoint detected was one that took place starting May 17, 2016. This one used spam emails that contained a link to a malicious file.
The emails tried to pass as Microsoft security alerts, and the downloaded file would install the Kronos trojan, first seen on the malware scene after July 2014. Besides Canadian targets, this Kronos campaign also went after Australian and US users.
The second campaign started on June 6 and used macro-laced Word files to download and install the notorious Dridex trojan.
The third campaign took place twenty days later, on June 26, and crooks employed Office files that were using OLE objects similarly to macros, which executed JavaScript code, which, in turn, downloaded and installed the Gootkit banking trojan. This campaign targeted banks from both Canada and Germany.
A fourth campaign was spotted just three days ago and employed spam posing as UPS notices, aimed at Canada and UK users. These emails came with Office files that asked the user to enable macros. Doing so would have infected victims with the Vawtrak banking trojan.
Two more campaigns that spread Ursnif and Zeus were also detected, but to a smaller degree.
Caution needed when dealing with spam email
While it may have been just a weird coincidence that all these campaigns targeted Canada at the same time, all users should be on the lookout for devious tactics when opening files from unknown senders. Proofpoint recommends the following:
“ Be vigilant when reading email messages that contain links or attachments. All of the campaigns described here relied on social engineering to trick users into infecting themselves with malware, even though their systems would have likely presented security warnings when they opened malicious files. ”
“ Never enable macros in documents that arrive via email or download and run executables linked from an email message unless you are absolutely certain the message is authentic. ”
“ Configure online banking accounts with maximum security settings. For example, enabling two-factor authentication and notifications or confirmation for any money transfers can often prevent losses even if a system is infected. ”
“ Organizations should also invest in appropriate security technologies to protect their employees from falling prey to these attacks. Businesses are particularly at risk because their bank accounts typically contain much larger amounts of money and are therefore a higher-priority target for attackers. Larger employee pools also increase the odds of a successful infection. ”

 14 DAY TRIAL //
14 DAY TRIAL //