The Superfish software piece is currently breaking the secure connection for at least 44,000 users of Firefox, as man-in-the-middle certificates signed by the application have been detected in Mozilla’s web browser.
The program is a browser add-on that was pre-loaded on Lenovo consumer notebooks between September and December 2014, but it is distributed through a variety of channels, such as bundled with the installation of a different program; as such, it affects a larger pool of users, not just Lenovo customers.
Classic man-in-the-middle attack
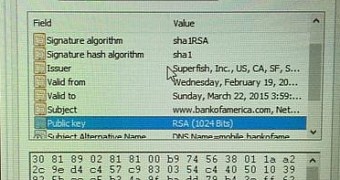
Recently, it has been discovered that it acts as a proxy between the user and an HTTPS website and that it uses a self-generated root certificate to sign any website using HTTPS, which is a classic man-in-the-middle (MitM) attack.
Because the root certificate is installed in Windows, web browsers relying on the OS’s certificate store will trust it implicitly.
The bigger issue is that certificates are signed with the same RSA key, and anyone recovering it could launch MitM attacks against users connecting to a compromised Internet gateway, such as a public Wi-Fi hotspot.
Cracking the RSA key encrypting the Superfish root certificate was already achieved on Thursday, by Robert Graham, CEO of Errata Security.
Mozilla implements its own certificate store, though, and it was believed that Firefox users would not be affected by Superfish’s MitM activity.
A much higher amount of users is affected
However, the Electronic Frontier Foundation (EFF) found the large number of certificates in Firefox, which disputes the theory that using this browser is safer on account of the fact that a different certificate store is used.
EFF made the discovery through its Decentralized SSL Observatory project, which collects data from Firefox instances with HTTPS Everywhere installed, an extension that forces usage of a secure connection to websites that support it but make it more difficult to access.
“This either indicates that Superfish also injects its certificate into the Firefox root store, or that on a large number of occasions Firefox users have been clicking through certificate warnings caused by Superfish MITM attacks,” EFF says in a blog post.
Since EFF’s information comes only from browsers equipped with the extension, chances are Superfish’s root certificate is installed on a much larger number of machines.
To mitigate the risk, users need to remove both the Superfish program and its root certificate. Mozilla provides instructions for deleting the certificate from its store and a guide from Lenovo explains the same process for Windows certificate store.
 14 DAY TRIAL //
14 DAY TRIAL //