IOActive researcher Ariel Sanchez has analyzed a total of 40 mobile banking applications for iOS devices to see if they’re secure or not. The apps belong to the 60 most important banks from all over the world.
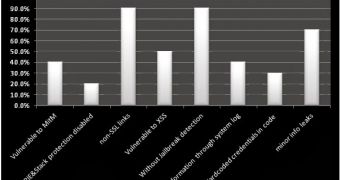
The expert has found that 40% of the tested apps are vulnerable to Man-in-the-Middle (MitM) attacks because they don’t validate the authenticity of SSL certificates.
Around 20% of them have the Position Independent Executable (PIE) and Stack Smashing Protection disabled, which makes them susceptible to memory corruption attacks.
90% of them don’t have jailbreak detection. The same percentage contain a number of non-SSL links when surfing the app, allowing cybercriminals to intercept traffic and inject arbitrary code for phishing purposes.
Cybercriminals can also abuse insecure UIWebView implementations in over half of the tested apps to inject JavaScript.
When it comes to two-factor authentication, which is a great mechanism to protect against impersonation attacks, the researcher has found that 70% of the iOS banking apps don’t have such a system.
It turns out that 40% of the applications expose sensitive information through log files, such as crash reports. The data leaked by the log files can be leveraged to develop zero-day exploits.
Interestingly, 30% of the tested programs contain hardcoded credentials in the code.
“By using hardcoded credentials, an attacker could gain access to the development infrastructure of the bank and infest the application with malware causing a massive infection for all of the application’s users,” Sanchez explained.
App activation codes, the ones sent during the initial setup process, could be highly valuable for cybercriminals, yet 20% of the reviewed pieces of software send the information in plaintext (HTTP).
Finally, the file systems of some programs store sensitive information, including bank account details and transaction history, in unencrypted databases.
It’s worth noting that all these vulnerabilities were found by testing the client side of the application. Some of the financial institutions whose mobile banking apps are vulnerable have been notified.
 14 DAY TRIAL //
14 DAY TRIAL //