Security researchers from Symantec have been monitoring CryptoDefense, a piece of ransomware that’s similar to the notorious CryptoLocker. Based on the Bitcoin addresses and blockchain information, experts estimate that CryptoDefense earns cybercriminals as much as $34,000 / €25,000 per month.
CryptoDefense is a relatively new piece of ransomware. It appeared in late February 2014, but Symantec’s products have already blocked over 11,000 unique infections.
Infections have been spotted in more than 100 countries. Most are in the United States, the United Kingdom, Canada, Australia, Japan, India, Italy and the Netherlands.
Similar to CryptoLocker, CryptoDefense encrypts the most important files on compromised computers and holds them that way until a ransom is paid by the victim. In order to secure its communications, the malware uses TOR. To make sure encrypted files cannot be recovered without paying the ransom, RSA 2048 encryption is used.
Symantec experts say the threat is being distributed with the aid of spam emails that purport to carry a scanned copy of a document.
When it’s executed, CryptoDefense connects to four remote domains to which it sends basic information on the infected device. Then, the files on the computer are encrypted and the private key is sent back to the server. Next, a screenshot of the compromised desktop is taken and uploaded to the cybercriminals’ server.
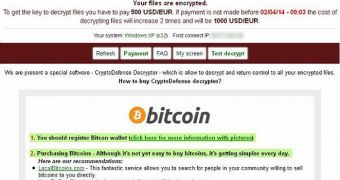
Instructions with the ransom demands are added to every folder containing encrypted files. Victims are told how to make the payment and how to recover their files. The attackers demand the payment of 500 USD/EUR. The cost doubles if the payment is not made within four days.
Fortunately for victims, there is a way to recover their files without paying the ransom. Although they’ve implemented RSA 2048 encryption, the developers have neglected one important aspect: the decryption key is not removed after being sent to the server.
“As advertised by the malware authors in the ransom demand, the files were encrypted with an RSA-2048 key generated on the victim’s computer. This was done using Microsoft’s own cryptographic infrastructure and Windows APIs to perform the key generation before sending it back in plain text to the attacker’s server,” Symantec experts explained.
“However, using this method means that the decryption key the attackers are holding for ransom, actually still remains on the infected computer after transmission to the attackers server,” they added.
“Due to the attackers poor implementation of the cryptographic functionality they have, quite literally, left their hostages a key to escape.”
Additional details on the CryptoDefense ransomware are available on Symantec’s blog.
 14 DAY TRIAL //
14 DAY TRIAL //