A distributed denial-of-service (DDoS) attack hit Sony servers on Sunday, and the hacker claiming responsibility for it says that one server was crippled by 263.35 Gbps of junk traffic.
News broke that a hacker collective going under the name of Lizard Squad directed a large DDoS attack against Sony Online Entertainment and PlayStation Network services.
However, it appears that the group’s contribution to the incident was to merely take credit for the deed and bring more attention to it by tweeting a bomb scare to the flight carrying SOE's president John Smedley from Dallas to San Diego.
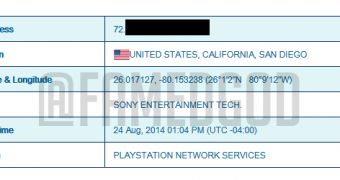
The attack seems to be the act of a hacker known on Twitter as Fame (@FamedGod), who came back with a vengeance plan, making public the IP addresses of every member of the Lizard Squad collective.
FamedGod tweeted that they pulled the DDoS by abusing NTP (Network Time Protocol) servers, which blasted 263.35Gbps of bad traffic towards one Sony server.
In the second quarter of 2014, the largest DDoS recorded by Arbor Networks was of 325 Gbps. Verisign also registered values peaking at 300 Gbps for the same time frame; by comparison, 263.35 Gbps is far from being a light blast.
Soon after launching the attack, users started to experience issues on the PSN service, being signed out due to an error (80710092) that signaled online connectivity problems.
According to companies offering DDoS mitigation solutions, amplification attacks carried out through NTP servers have become more frequent in the second quarter of the year.
In the case of the Sony incident, FamedGod appears to have leveraged vulnerable NTP servers. “OMG my NTP Lists are dead already. Gotta scan for new ones,” a tweet says.
A report in May regarding the number of NTP servers vulnerable to the “monlist” function abuse informed that 17,647 machines still needed to be patched; out of these, more than 2,100 were capable of an amplification of at least 700x.
In a YouTube video, the hacker explains that the attack was possible because Sony did not implement sufficient security measures to its network following the 2011 incident, which resulted in the theft of personal details from about 77 million user accounts.
FamedGod explains that “jailbreaks can access hidden and prohibited content now” and that the address of the attacked server could be discovered by decrypting a memory dump. “Memory dumping can reveal the hidden servers which personal and main information is stored. Simple hex converting and decryption lead to a full DDoS on playstations main server data center,” it is said in the video.
A good example to follow is Microsoft’s Xbox network, which does not operate on a single datacenter.
The Twitter feed of the hacker also contains a post saying that Sony could task a team with monitoring servers and filtering the bad traffic from a DDoS attack, but they would not spend the money on this.
263.35 Gbps Attack sent to a sony server. RIP Bitches. Another Month of Maintenance.
— Fame (@FamedGod) August 24, 2014
Check out FamedGod's explanation of the attack:
 14 DAY TRIAL //
14 DAY TRIAL // 