Control over the entire network traffic without being detected can be achieved using a device called USBdriveby, which is in essence a $20 / €16 Teensy micro-controller (3.1) programmed to emulate keyboard strokes and mouse action.
Computer hacker and security researcher Samy Kamkar developed the code that enables the device to change the settings of an operating system to allow complete control of the machine, the entire procedure being completed in mere seconds.
The Teensy micro-controller is a USB-based development system board that can be used for different projects, all programming being done via the USB port.
USBdriveby activity can evade detection
The device programmed by Kamkar behaves like a keyboard as soon as it is plugged into an unlocked computer. In a video demonstration he shows how USBdriveby could be used to change the DNS settings of a system, a type of attack that can be employed to serve fake web pages to a victim, tricking them into disclosing private information or downloading malicious software.
The demonstration was made on OS X, but the researcher says that the code for Windows and Linux can be easily created.
In the example offered, he evades OS X security that prevents making network-related changes, such as DNS settings, with only the keyboard and forces usage of the mouse, too. By enforcing this measure, the system “knows” that the modifications are not done through an automated process, which is generally associated with malicious activity.
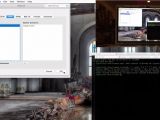
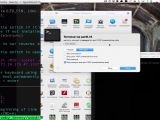
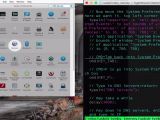
As soon as USBdriveby was inserted in the computer, a terminal window was launched and then a connection to a specific server was initiated. If a firewall is present, the device can emulate a keyboard to allow the connection.
In the next steps of the attack, Kamkar downloaded a backdoor program and set the address of the primary name server to one under his control. All the windows were automatically closed after the changes were made. The result of the experiment was spoofing Facebook.com, serving a fake page to the victim.
Keeping safe is not that complicated
Teensy is not the only micro-controller that can be used for this type of task, and Arduino micro-controllers also fit the bill, although not all of them, the researcher explains.
Protecting against this type of attack is possible, and it is not a complicated job. First of all, an attacker needs physical access to the computer, which has to be unlocked.
As such, a password-protected screen saver would ensure that USBdriveby cannot be used; but this kind of computer state cannot be always guaranteed, as Kamkar explained in an email conversation.
Whitelisting USB devices that can be connected to the computer would also seem like a feasible solution, but the developer told us that “preventing a ‘keyboard’ from working on a machine can be tough -- even if you do block by VID/PID numbers, a USB device can enumerate those, spoofing the device.”
His recommendation is to apply multiple security gates for users trying to access the computer. On the other hand, this can be defeated if poorly designed, he said.
Check out the demo video for USBdriveby:

 14 DAY TRIAL //
14 DAY TRIAL //