There's a reason why a large piece of the Internet went down last week after a DDoS attack on a key DNS service provider, and that is poor equipment design.
While Internet of Things (IoT) devices such as DVRs, CCTV systems, IP cameras, baby monitors, and others are to blame and have played a major role in recent DDoS attacks, there is another type of equipment that also regularly contributes to DDoS botnets.
Those devices are home (SOHO) routers, which some experts wrongfully categorize as IoT when they're just your regular networking equipment that's been around for years before the concept of IoT even appeared.
You'd think that because hardware manufacturers have been building such devices for so long, they'd know how to do it by now. Unfortunately, you're wrong, because these companies put costs above everything else, and security always takes a backseat in exec boardrooms.
As such, we have millions of insecure routers all over the globe, which can easily be turned against us.
ESET scanned 12,000 routers
Slovakian cyber-security firm ESET has set out to find out how many of these routers are improperly designed. With data from 12,000 customers that have agreed to share details about their home routers, ESET paints a grim picture of the router landscape.
After performing local scans and aggregating all the details, ESET says it discovered that 15 percent of all tested routers used a weak factory-default password that can be easily brute-forced.
If that wasn't bad enough, ESET also discovered that 20 percent of the tested routers exposed their Telnet port to the Internet, which is like a big red blinking sign pointing to your router.
One in ten routers runs faulty firmware
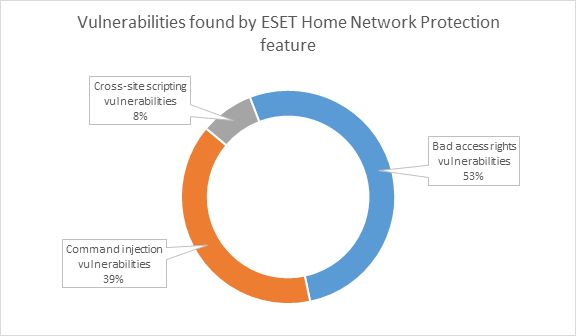
An additional 7 percent of routers also run firmware that includes medium and high severity vulnerabilities, which attackers can exploit to take over the device.
Of these vulnerabilities, the vast majority, 53 percent, are so-called bad access rights flaws, or authentication bypasses that allow an intruder to access parts of the router's management console where they shouldn't be able to reach.
Another large chunk of flaws, 39 percent, are command injection vulnerabilities that allow an attacker the chance to execute code on the router, a situation just as dangerous as the first.
"The results clearly show that routers can be attacked fairly easily, by exploiting one of the frequently found vulnerabilities," ESET's Peter Stancik says. "This makes them an Achilles heel in the overall internet security of households, as well as small businesses."

 14 DAY TRIAL //
14 DAY TRIAL //