Two scientists from Northeastern University carried out an experiment on the Tor Network, introducing 1,500 honeypot servers that revealed at least 110 Tor HSDirs (Hidden Services Directories) are probing fellow Tor relays and even attempting to exploit security weaknesses.
The experiment, which took place between February 12, 2016, and April 24, 2016, was started to test the trustability factor of fellow TOR servers, and most especially, HSDirs, which is a more complex term for a Tor server hosting a (Dark Web) .onion website.
HOnion servers snooped on Tor traffic for 72 days
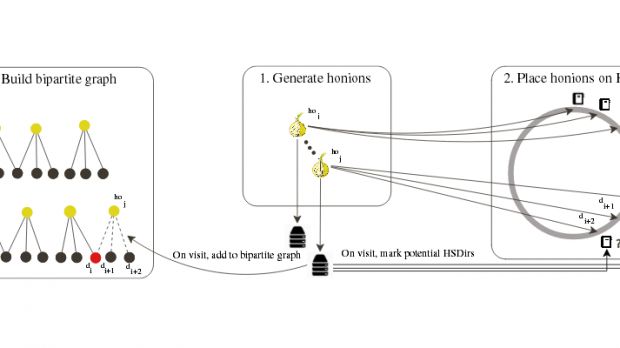
The researchers introduced honeypots, which also functioned as real-life Tor servers, called HOnions, running a framework for detecting abnormal Tor traffic.
The servers were introduced gradually into the network, in order to cover as much of the Tor traffic exchanged through the network.
After 72 days, the researchers gathered and analyzed all their data, and presented the study's results at the Privacy Enhancing Technologies Symposium, last Friday.
The two researchers, Professor Guevara Noubir and Ph.D. student Amirali Sanatinia, revealed they identified at least 110 HSDirs showing out of the ordinary behavior.
Some servers attempted SQL injection and XSS exploits
While most queried for data such as server root paths, description.json server files, and the Apache status page, there were some that exhibited downright malicious behavior.
“ [W]e detected other attack vectors, such as SQL injection, targeting the information_schema.tables, username enumeration in Drupal, cross-site scripting (XSS), path traversal (looking for boot.ini and /etc/passwd), targeting Ruby on Rails framework (rails/info/properties), and PHP Easter Eggs (?=PHP*-*-*-*-*). ”
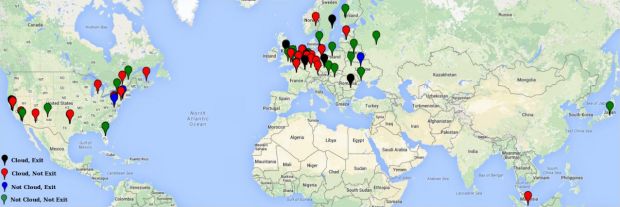
Over 70 percent of these 110 misbehaving HSDirs were running on professional cloud infrastructures, showing an actor who invested into setting up the nodes, not your average Joe hacker setting up their home desktop as a Node server.Some malicious servers were Tor exit nodes
Furthermore, 25 percent of the 110 HSDirs also functioned as exit nodes for Tor traffic, raising the alarm that they might be carrying out MitM attacks, and snooping on Tor traffic.
Attacks on the Tor network are nothing new for the Tor Project, who's been probed by both nation-state actors, official crime investigation agencies, academic researchers, and cyber-criminals alike.
Below is a map of the malicious Tor HSDirs discovered during the research. The full study is also available online under the title of HOnions: Towards Detection and Identification of Misbehaving Tor HSDirs.
UPDATE [July 26, 2016]: The Tor Project has responded to these findings via an official blog post.
 14 DAY TRIAL //
14 DAY TRIAL //