A cyber-espionage campaign believed to be sponsored by the Chinese government has been running against targets in ASEAN (Association of Southeast Asian Nations), changing little in the attack toolkit and the infrastructure used since its initial deployment in 2005.
The objective of the operation is to exfiltrate from the targets sensitive information for political gain. Entities of interest were those involved in regional politics, military and economic problems, as well as media organizations and journalists reporting on topics tied to the Chinese government.
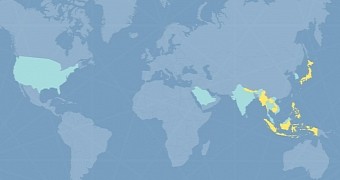
Among the countries where APT30 activity has been confirmed there is India, South Korea, Thailand, Malaysia, Saudi Arabia, Vietnam, and the US.
Air-gapped systems targeted by APT30
Named APT30 by researchers at FireEye, the group of hackers relied on malware downloaders, backdoors and a central controller to carry out its business.
The researchers point out that APT30 used three pieces of malicious software (SHIPSHAPE, SPACESHIP, and FLASHFLOOD) that would infect removable drives and thus could expand its reach to hosts that cannot be contacted directly via Internet.
The experts believe that these tools were built specifically for stealing information stored on air-gapped networks. The compilation date of one of the samples (FLASHFLOOD) encountered is from 2005, while the earliest build time for the other two dates from 2006.
According to FireEye’s analysis, the command and control (C&C) software suggests that the threat actor prioritized its targets and worked in shifts to maintain a constant eye on the operation and the new developments.
Domains registered in 2004, backdoor created in 2005 is still in use
The group’s prolonged activity was determined by checking the domain registration dates, which go as far back as 2004.
“Typically, threat groups who register domains for malicious use will abandon them after a few years. APT30, however, has used some of their domains for more than five years, with some of their earliest domains still in use as of at least late 2014,” the researchers say in a technical report on the activity of the group.
Further evidence supporting the long-lasting infrastructure is given by a backdoor sample compiled by the group in 2005, which used “km-nyc[.]com” as its primary C&C server. The same domain was found to be used by a newer sample, with November 5, 2014 as the compilation date.
The researchers observed that the main malware (backdoors BACKSPACE and NETEAGLE, and the pieces intended for removable storage drives) remained the same over time and their code was adapted to suit the threat actor’s needs as they appeared. FireEye says that backdoors with versions dating from 2005 are still in use today.
“This dedication to adapting and modifying tools over a number of years, as opposed to discarding old tools in favor of newer, readily available ones, implies that APT30 has a long-term mission, and that their mission is consistent enough for their existing tools to be sufficient to support their operations over a long period of time,” FireEye adds.
 14 DAY TRIAL //
14 DAY TRIAL //