Synolocker crypto-malware affecting Synology network access (NAS) devices in particular, has hit the Faculty of Medicine of Chinese University and took hostage no less than 10,000 patient records.
It appears that the affected data belongs to the Centre for Liver Health and Institute of Digestive Disease at the Prince of Wales Hospital in Sha Tin, and the police confirmed that the crooks used Synolocker for the deed.
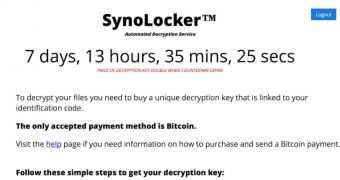
Just like in other cases, the ransom fee for receiving the private key that can decrypt the data is 0.6 Bitcoin ($350 / €260).
According to South China Morning Post, there is no evidence that the data has transpired from the storage devices, so there is no apparent risk of exposure.
As soon as the infection was discovered on the affected systems, they were immediately taken offline to avoid propagation of the threat.
At the moment there is no information on how the department plans to recover the files, or if a backup copy of the data exists, which would makes it possible to restore it.
Attacks leveraging Synolocker ransomware have started more than a week ago, when the members of the Synology forum reported that their systems could no longer be accessed, receiving instead a ransom message asking them to pay for releasing their data.
Some methods to partially rescue the files as they are encrypted have been found to be efficient, but users are advised to take precautions such as changing the connection port, disabling SSH and Telnet services and strengthening the log in password in order to reduce and even eliminate the risk of infection.
 14 DAY TRIAL //
14 DAY TRIAL //