One in every three PCs infected with malware is a zombie computer, namely a machine that is part of a botnet and controlled by a remote attacker with as much if not even more privileges than the user sitting in front of the screen. Data from the Microsoft Security Intelligence Report (SIR) volume 9 delivers insight on the global botnet problem and the cybercriminals controlling networks of zombie computers.
As if necessary, the report is a perfect argument for the introduction of new security measures that can protect not only end users, but also the Internet and critical infrastructure that’s connected to the world wide web.
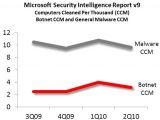
“If you compare the worldwide infection rate of computers cleaned per thousand (CCM) as detailed in the botnet section of SIR v9 with the general malware CCM, an interesting picture emerges,” revealed Microsoft’s Ina Ragragio.
“By Q2 of this year, one out of every three infected machines were part of a botnet. So, if you've been hit by any malware recently, there's a 33% chance that it was by a bot, or that a bot was installed on your machine in addition to that malware.”
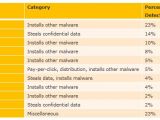
Zombie computers are being used for a variety of illegal activities online without the end users being aware of the fact that their PC is controlled remotely by a cybercriminal.
Attackers can leverage botnets to send spam, for phishing attempts, for Denial of Service (DoS), but also for online fraud, sensitive data theft. In addition, botnets can be used as a distribution channel for new malicious code.
“That's where botnets come in. Win32/Waledac, one of the largest botnets, is not only known as one of the most notorious spamming bots ever, it is also known to download and install rogue antivirus software, such as Win32/FakeSpypro, on the compromised computer,” Ragragio added.
“Most bot families, including Win32/Alureon, Win32/Hamweq, and Win32/IRCbot, are capable of downloading and executing arbitrary files, which may be configured to be malware.”
Microsoft recently proposed that a Public Health model be tailored and applied to the Internet in order to increase security.
According to the Redmond company, there’s a need for infected computers to be quarantined from the web until they are clean.
Such a model will certainly benefit the vast majority of users which are unequipped and lack the necessary IT skills to protect their computers against attackers and malware.
“Regardless of how botnets are doing their distribution, one thing is clear: because of their networked and often organized structure, they allow malicious and illegal activities to be performed at a scale that has not been seen before,” Ragragio said.
“The solution to this problem isn't always about technology. As a community, we can take collaborative and legislative action to take down massive botnets like we did with Waledac. As researchers, we must evolve the way we view these threats and continue to think of creative and novel ways to stop them.”

 14 DAY TRIAL //
14 DAY TRIAL //