- Security Blog
- Hacking News
- Virus alerts
- Data Breaches
- Incidents
- Security Fixes and Improvements
- Spam Reports
- Advisories
- Server related
- Cyber Espionage
- Spyware Threats
- Weekly Roundup
- By Eduard Kovacs
- April 14th, 2012

Operation Blitzkrieg: Extremists Offer Reward for Information on Hackers
Anonymous hackers are more determined than ever to attack Nazis
- By Eduard Kovacs
- April 14th, 2012

Crooks Push Malware as “Tibetan Input Method for Apple iOS 4.2 Devices”
Cybercriminals rely on malware hybridization to ensure the success of their campaigns
- By Eduard Kovacs
- April 14th, 2012

Sites of Brazilian Federal Police Attacked by Anonymous
DDOS attacks against the police were launched using web-based tools
- By Eduard Kovacs
- April 14th, 2012
Researchers Reveal Flaws in Microsoft Partner Network Cloud Service
Microsoft Afkar was found to contain a cross-site scripting flaw
- By Eduard Kovacs
- April 13th, 2012

Expert Reports SQL Injection Flaws in Barclay Simpson Site
Barclay Simpson representatives have failed to respond to our inquiry
- By Eduard Kovacs
- April 13th, 2012

OpDefense: Financial Services Roundtable Site Brought Down
Social media websites are buzzing with "tango down"
- By Eduard Kovacs
- April 13th, 2012

EP Rapporteur to Recommend Rejection of ACTA
Europe takes another step back from the controversial treaty
- By Eduard Kovacs
- April 13th, 2012

Sabu Refuses to Go to Court After Receiving Physical Threats
It's not easy to live your life after you've upset thousands of hackers
- By Eduard Kovacs
- April 13th, 2012

Experts Release Android App That Can Harvest Data Without Permissions
A simple app can access the SD card, device identifiers and other data
- By Eduard Kovacs
- April 13th, 2012
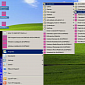
Ransomware Accuses Users of Piracy and Encrypts Files
Victims must be extra cautious because they can permanently lose their files
- By Eduard Kovacs
- April 13th, 2012

Ransomware Infects Master Boot Record
Once the victim pays a fine the MBR is cleaned up
- By Eduard Kovacs
- April 13th, 2012

Team Dig7tal Hackers Leak Data from Harvard University's SEAS
The administrator's login credentials have been published online
- By Eduard Kovacs
- April 13th, 2012

Operation Defense: Boeing Site Attacked by Anonymous, More to Follow
Anonymous has made the list of future targets available
- By Eduard Kovacs
- April 13th, 2012
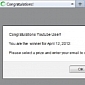
Typosquatters Rely on Tumblr to Serve Bogus Surveys
Users who type "Tublr.com" may find themselves on a shady website
- By Eduard Kovacs
- April 13th, 2012

Israeli Spies Planted Stuxnet Using Infected Memory Stick
This approach was considered to be more effective
- By Eduard Kovacs
- April 13th, 2012

TeaMp0isoN Members Arrested, Hackers Deny It
Two alleged hacktivists have been detained by the Metropolitan Police
- By Eduard Kovacs
- April 13th, 2012

Scotland Yard Denies MI6 Hack Claimed by TeaMp0isoN
Authorities state that the conversation was obtained via the receiving handset