- Security Blog
- Hacking News
- Virus alerts
- Data Breaches
- Incidents
- Security Fixes and Improvements
- Spam Reports
- Advisories
- Server related
- Cyber Espionage
- Spyware Threats
- Weekly Roundup
- By Eduard Kovacs
- July 11th, 2012
Backdoor Served on Colombian Site Affects Mac, Windows and Linux Users
A malicious .jar file serves a piece of malware after determining the platform
- By Eduard Kovacs
- July 11th, 2012

Corporate Espionage: Cybercriminals Plant USB Sticks in Firm’s Parking Lot
If the usual hacking methods don't work, things can become more physical
- By Eduard Kovacs
- July 11th, 2012

Thousands of Sites Possibly Hacked by Exploiting Plesk Zero-Day
An exploit is being sold on underground forums for the price of $8,000 (6,300 EUR)
- By Eduard Kovacs
- July 11th, 2012

Microsoft Addresses XML Core Services Remote Code Execution Vulnerability
A Fix It solution that disables Windows Sidebar and Gadgets has also been made available
- By Eduard Kovacs
- July 10th, 2012

Researchers Identify “Invisible” Data Theft at Black Hat USA 2012
Stochastic forensics can be used to determine if data was copied from a computer
- By Eduard Kovacs
- July 10th, 2012

NSA Chief at AEI: Cyber Security, Spying and China
General Alexander claims that the agency doesn't store data on US citizens
- By Eduard Kovacs
- July 10th, 2012

ICS-CERT Warns of Malware That Spreads via USB Drives
In April, a virus almost penetrated the systems of an energy company
- By Eduard Kovacs
- July 10th, 2012

Imperva Releases Scuba 2.0 and SecureSphere 9.5
Great tools for data warehouses and enterprise databases
- By Eduard Kovacs
- July 10th, 2012

ENISA Makes Recommendations for the Successful Roll-Out of Smart Grids
Cyber security measures are a necessity for anything that relies on computer networks
- By Eduard Kovacs
- July 10th, 2012

Man-in-the-Mobile Attacks Target the Bank Accounts of Android Users
Individuals from Spain, Portugal, Germany and the Netherlands are potential victims
- By Eduard Kovacs
- July 10th, 2012

Hacked Road Sign Displays “Impeach Obama” Message
From now on, the Department of Transportation will secure them better
- By Eduard Kovacs
- July 10th, 2012

Stay Secure: Useful Tips for Online Gamers
A great advisory for both casual and hardcore players
- By Eduard Kovacs
- July 10th, 2012

Best Buy: Hackers Are Using Stolen Credentials to Access Customer Accounts
The company has started advising customers to change their passwords
- By Eduard Kovacs
- July 10th, 2012

Scam: World Trade Register Business Registration Is “Free”, but It Costs a Lot
Misleading offers and newly registered domains indicate the presence of a scheme
- By Eduard Kovacs
- July 10th, 2012
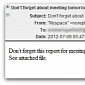
“Don’t Forget About Meeting Tomorrow” Emails Carry Malicious “Report.Zip”
The messages are cleverly designed to avoid email filtering systems
- By Eduard Kovacs
- July 10th, 2012

Personal Details of 8,000 Australian Stay Smart Online Users Lost in Postal System
AusCERT sent a DVD to the DBCDE via physical mail, but the package never arrived
- By Eduard Kovacs
- July 10th, 2012

Cyberoam Issues Hotfix to Generate Unique CA Certificates for DPI Devices
The decision came after a user managed to obtain a private key