- By Eduard Kovacs
- January 27th, 2014

San Jose Police Might Tap into People’s Security Cameras to Solve Crimes
A councilman has made the proposition in an effort to make the city safer
- By Eduard Kovacs
- January 22nd, 2014
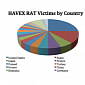
Russia Accused of Conducting Global Cyber Espionage Campaign
A group dubbed Energetic Bear is stealing sensitive information for Russia's economic gain
- By Eduard Kovacs
- January 20th, 2014
EFF Staff, AP Journalist and Activists Targeted in Vietnamese Espionage Campaign
The EFF has analyzed some of the attacks apparently carried out by state-sponsored actors
- By Eduard Kovacs
- January 6th, 2014

UAE Concerned About Backdoors in US-Made Components of French Satellites
The $930 million (€683 million) deal might fall through
- By Eduard Kovacs
- December 30th, 2013

NSA Uses Sophisticated QUANTUM Tools in Hacking Operations
The tools are linked to a shadow network operated by the agency
- By Eduard Kovacs
- December 7th, 2013

FBI Uses Malware to Track Down Iranian Man Suspected of Making Bomb Threats
Another example of how US authorities use surveillance software
- By Eduard Kovacs
- December 6th, 2013

FTC Cracks Down on Android Flashlight App Developer for Sharing Users’ Data
The company is accused of deceiving customers about how their data is collected and shared
- By Eduard Kovacs
- November 20th, 2013

Your LG Smart TV Is Spying on You, Even If You Tell It to Stop
Online behavior, search keywords and even file names stored on USB drives are collected
- By Eduard Kovacs
- November 2nd, 2013
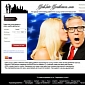
Fake LinkedIn Profiles Could Be Used to Gather Intelligence for Targeted Attack
Websense experts have analyzed a profile that lures users to a dating website
- By Eduard Kovacs
- August 2nd, 2013
![FBI Uses Hacker Tools to Tackle Organized Crime and Terrorism [WSJ] FBI Uses Hacker Tools to Tackle Organized Crime and Terrorism [WSJ]](https://news-cdn.softpedia.com/images/news2/FBI-Uses-Hacker-Tools-to-Tackle-Organized-Crime-and-Terrorism-WSJ-1.jpg)
FBI Uses Hacker Tools to Tackle Organized Crime and Terrorism [WSJ]
Spy software is never utilized against cybercriminals
- By Eduard Kovacs
- July 19th, 2013

Former NSA Director: Huawei Is a Threat to the National Security of Australia and the US
Huawei argues that there’s no evidence to back the accusations
- By Eduard Kovacs
- July 11th, 2013

Blue Coat Surveillance Devices Used in Iran, Syria and Sudan, Experts Find
Citizen Lab has published a comprehensive report on the topic
- By Eduard Kovacs
- July 9th, 2013

iOS and Android Apps Are Equally Intrusive, Bitdefender Study Shows
The IT security firm has used its Clueful technology to analyze mobile applications
- By Eduard Kovacs
- July 3rd, 2013

Motorola Phones Silently Send User Data, Passwords to Company’s Servers
Twitter, Facebook, Picasa and YouTube credentials are collected
- By Eduard Kovacs
- June 18th, 2013

Android Apps That Ask Permission to Collect Excess Data Are as Bad as Ones That Actually Collect It
Bitdefender has published a new study based on the company's Clueful technology
- By Eduard Kovacs
- June 6th, 2013

UK Concerned That Huawei Entered Critical Infrastructure Without Being Properly Vetted
The Intelligence and Security Committee has published a new report
- By Eduard Kovacs
- June 4th, 2013

NetTraveler Espionage Campaign Makes 350 High-Profile Victims in 40 Countries
Around 50 Chinese-speaking individuals are behind the operation